Hackers are duplicating website contact forms and discussion forums from reputable websites and pushing these forms via fake emails to unsuspecting users. These forms are very well made and are used to distribute Excel XLL files that download and install the RedLine password and information-stealing malware.
The forms can install malaware which steals data, RedLine can execute commands, download and run further malware, and create screenshots of the active Windows screen.
Spamming contact forms and discussion forums
This is a widespread campaign targeting many websites using public forums or article comment systems. Some fake emails ( aka phishing ) contain fake websites to host the malicious Excel XLL files used to install the malware.
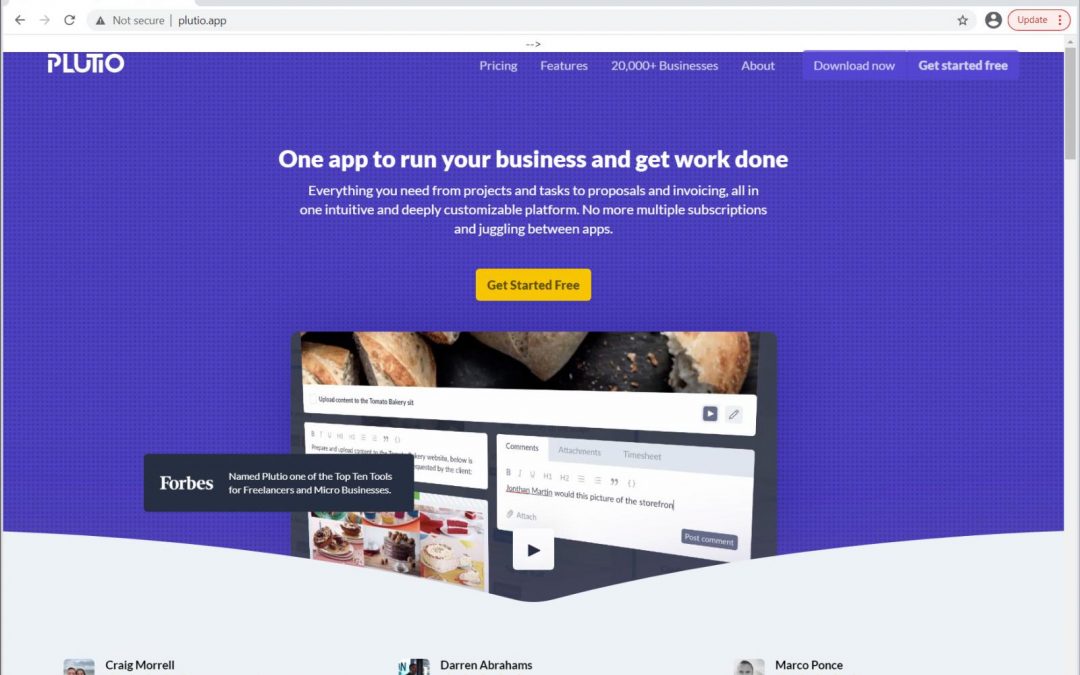
For example, one campaign used the following spam message and a fake website that imitated the legitimate Plutio site.
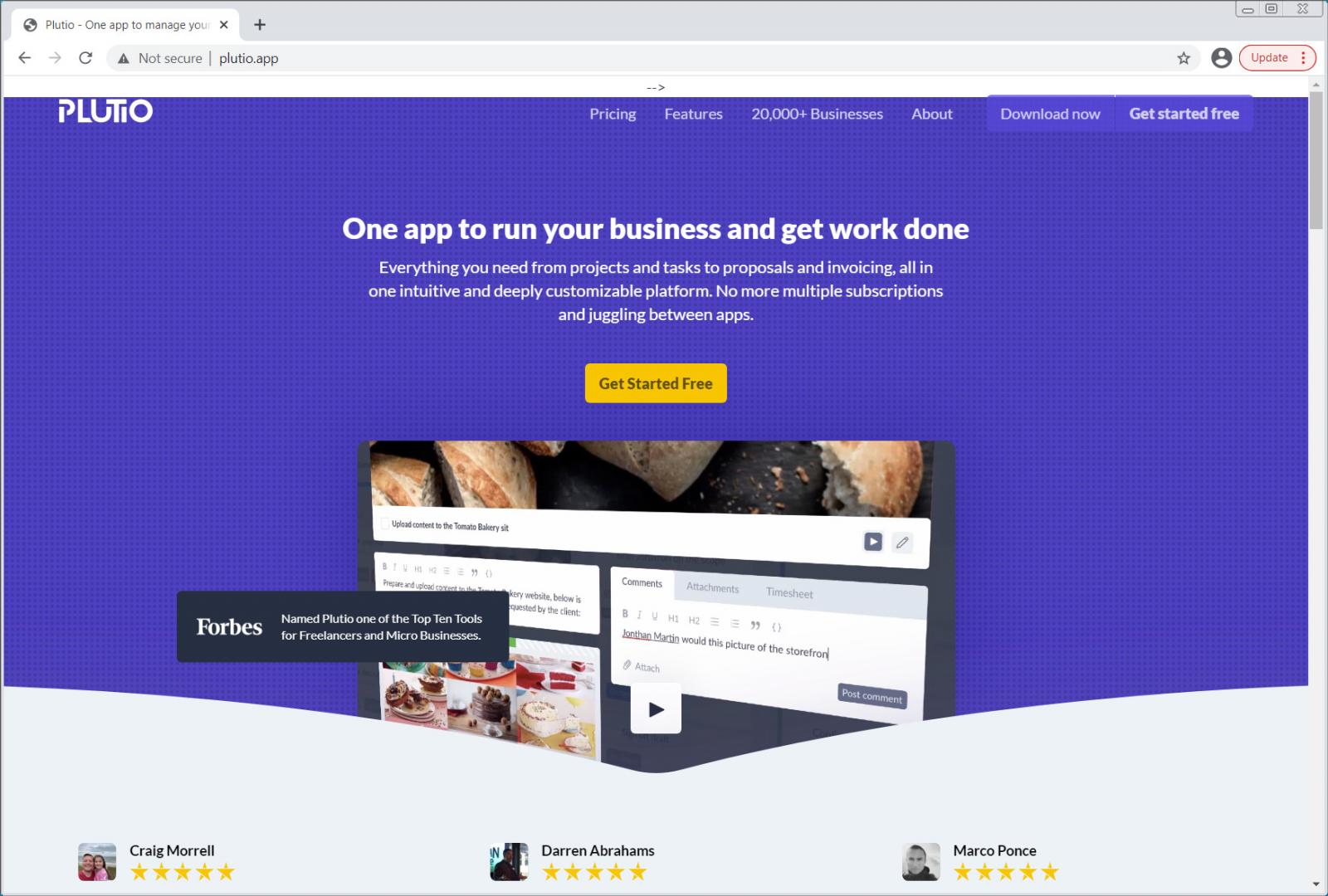
Other fake emails pretend to be payment reports, requests for advertising, or gift guides with links to malicious XLL files hosted on Google Drive, as shown below.
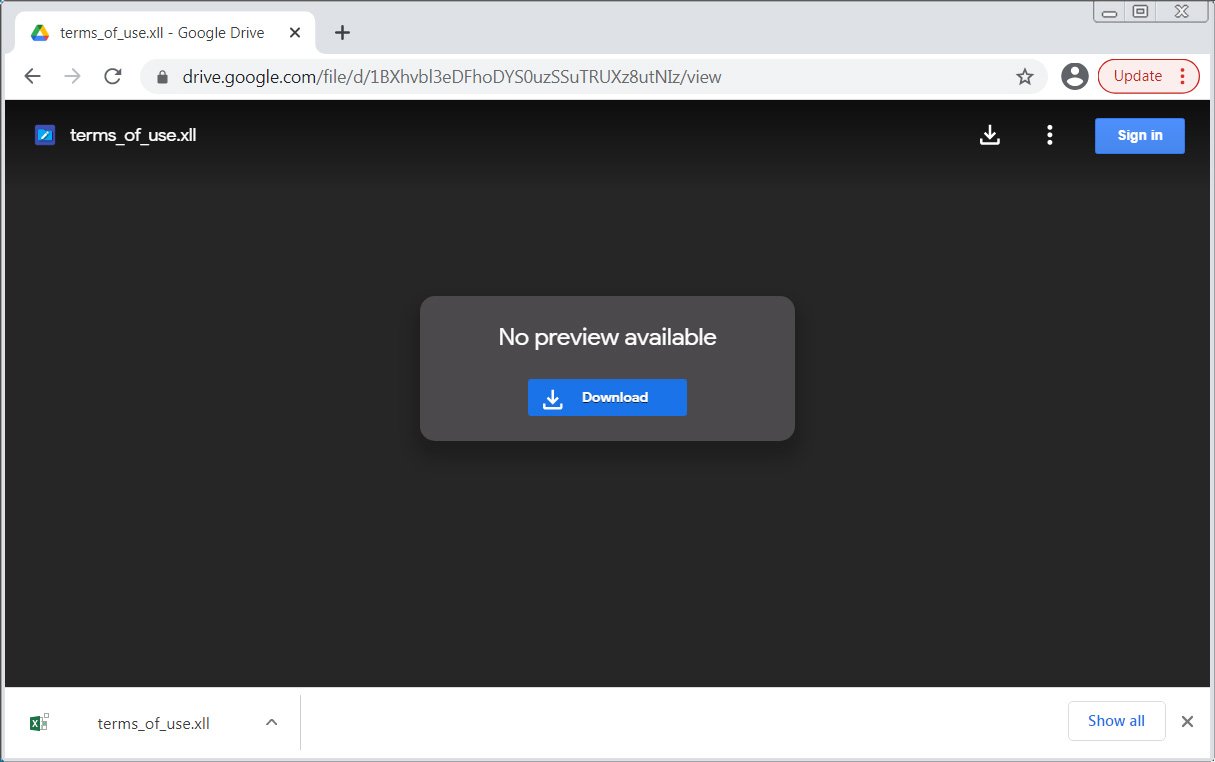
Abusing Excel XLL files
These spam emails are designed to execute harmful Excel XLL files that install RedLine malware on your windows computer.
An XLL file ( excel link library ) is an add-in code which extends Excel by reading and writing data, importing data from other sources, or creating custom functions to perform various tasks.
XLL files are simply a DLL file that includes an ‘xlAutoOpen’ function executed by Microsoft Excel when the add-in is opened.
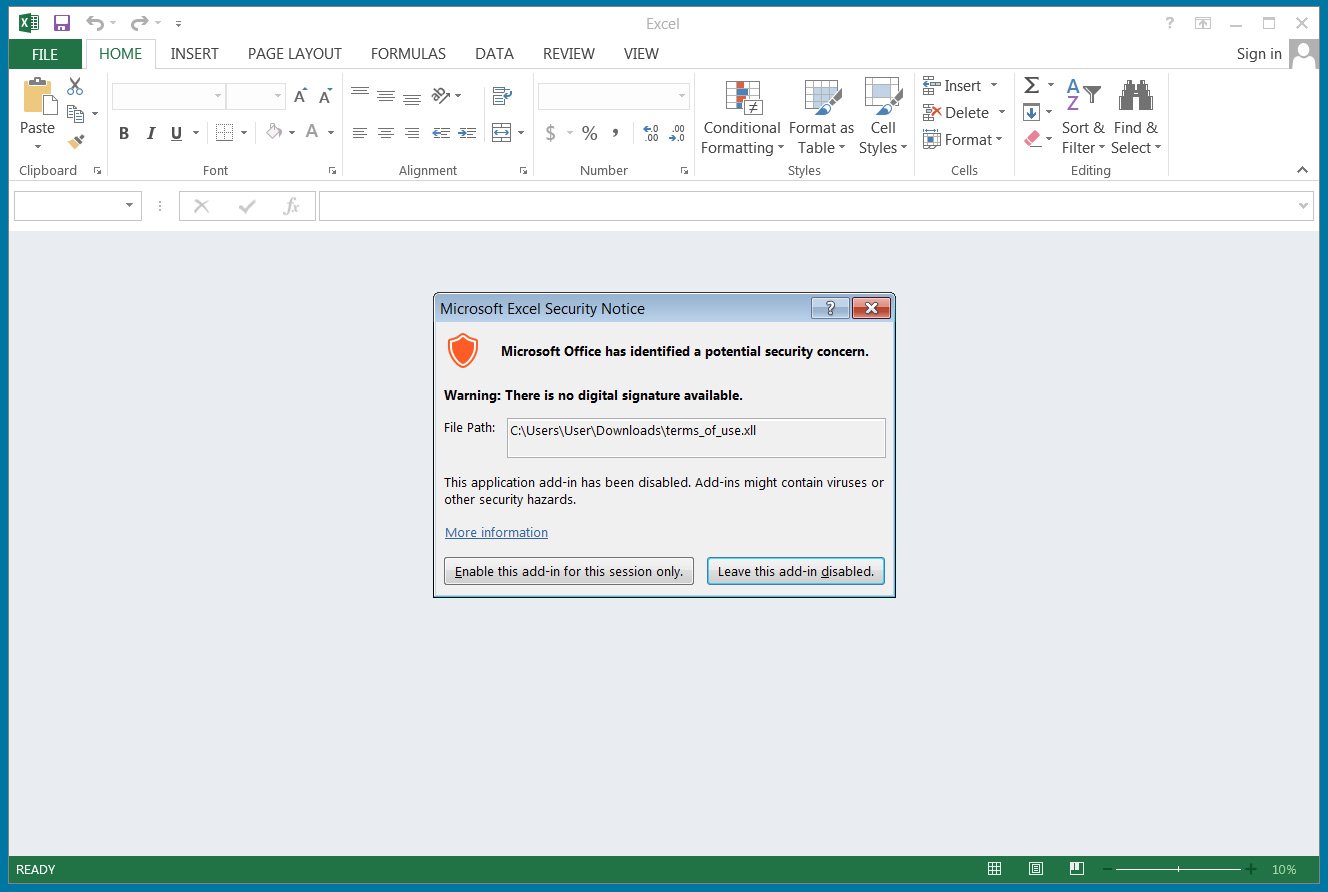
Once the malware runs, it will search for data to steal, including credentials and credit cards stored in the Chrome, Edge, Firefox, Brave, and Opera browsers.
If you have already been compromised you should assume that your stored passwords are freely available and immediately change them. Any credit card stored will be on-sold.
As XLL files are executables, threat actors can use them to perform a variety of malicious behavior on a device. Therefore, you must never open one unless it comes from a trusted source.
These files are not generally sent as attachments but instead installed through another program or via your Windows admin.
Therefore, if you receive an email or other message distributing these types of files, simply delete the message and report it as spam.
To see more of our IT Services c;lick attached link. Click here for more about our Virus Removal